
Post Finance picks Cilium for Cloud Native Networking
Cilium helped the Post Finance team build a scalable Kubernetes platform which meets the demanding requirements to run mission-critical banking software in production.
Watch The Case StudyRegulatory oversight is a hallmark of the financial industry. Cilium's detailed traffic monitoring and logging mechanisms support institutions in establishing transparent audit trails, complying with stringent regulations, and conducting forensic investigations.
The world of fintech revolves around APIs – from mobile banking apps to trading platforms. Cilium's API-aware network security ensures that these critical APIs can be secured, empowering teams with the toolsets needed to understand and guard against malicious patterns in API calls. Cilium supports L7 policies (e.g., allow HTTP GET /foo) for fine-grained access control to shared API services running common cloud native protocols like HTTP, gRPC, Kafka, etc. Cilium also supports deny-based, cluster-wide, and host-layer firewall network policies.
With Cilium, companies in the financial services industry can achieve improved observability, maintain security controls, and weave compliance and security governance for Kubernetes environments directly into the DevOps process.
We started by looking at some other tools, and we first used [the cloud provider CNI]. But we found that Cilium, with its host-based policies and its ability to replace what we had out of the box, was really valuable.
Bloomberg successfully enhanced the security and access control of its BQuant Enterprise workloads through the implementation of robust network security measures.
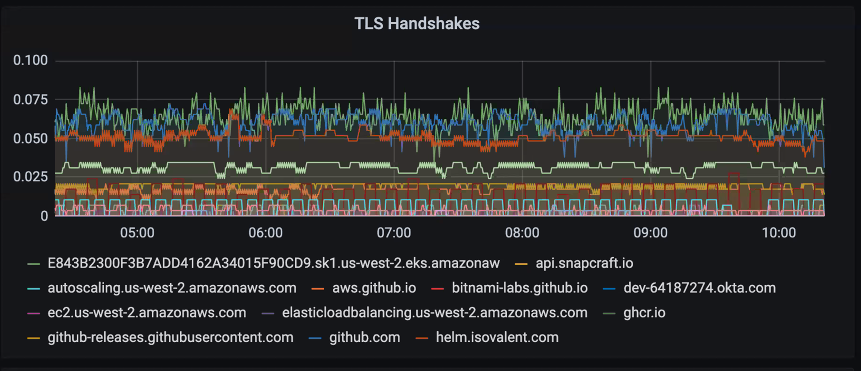
read the case studyIn a highly regulated industry such as financial services, ensuring that software and systems comply with these regulations is a constant challenge for development and operations teams. Cilium empowers teams with tools to ensure continuous compliance with standards like FIPS, PCIDSS, Open Banking, Fedramp, and SOC 2 by offering real-time monitoring and analysis of workload communication to identify non-compliant connections. It emphasizes encryption, traffic analysis, and full-stack monitoring without imposing performance constraints, ensuring confidentiality, integrity, and availability in regulated environments.
Post Finance one of Switzerland's leading financial institutions uses Cilium for Cloud Native Networking
watch the case studyAdopting a Zero Trust-based approach to network security architecture is essential for companies in the financial service industry to maintain compliance with stringent regulations and keep customer data secure.
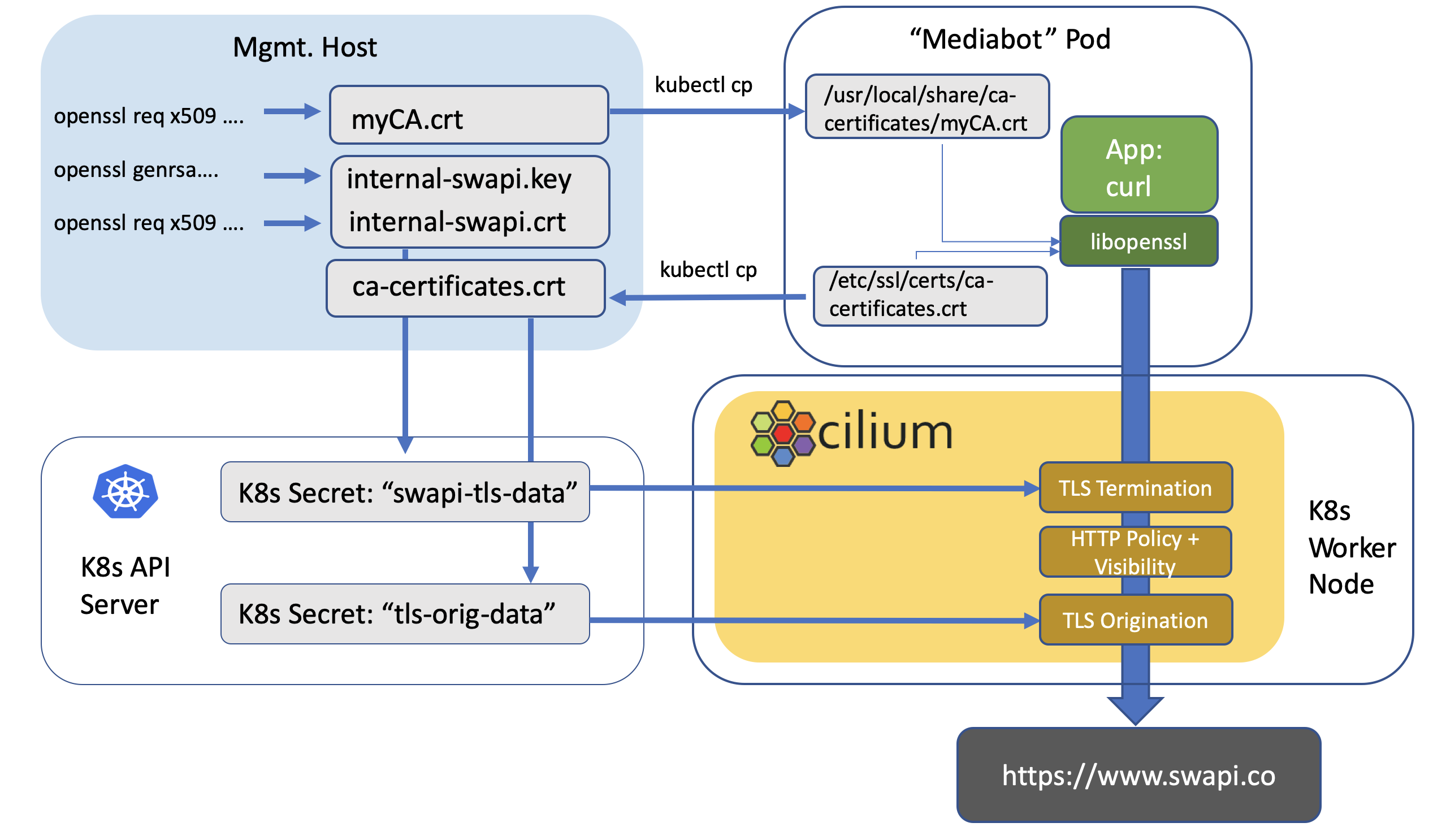
Cilium provides a unified tool that implements a range of features to enforce Zero Trust networking security principles. These features include identity-aware service to service communication and observability, advanced network policies with native HTTP and DNS protocol support, transparent encryption using in-kernel IPsec or WireGuard. Enforcement of TLS via Network Policy allows operators to restrict the allowed TLS SNIs in their network, and provide a more secure environment. Powerful security observability and real-time runtime enforcement with Tetragon and cluster-wide network policies provide security guardrails while having more specific policies to secure the application and operating system access control on different levels such as system calls, TCP/IP, file access, and namespace.
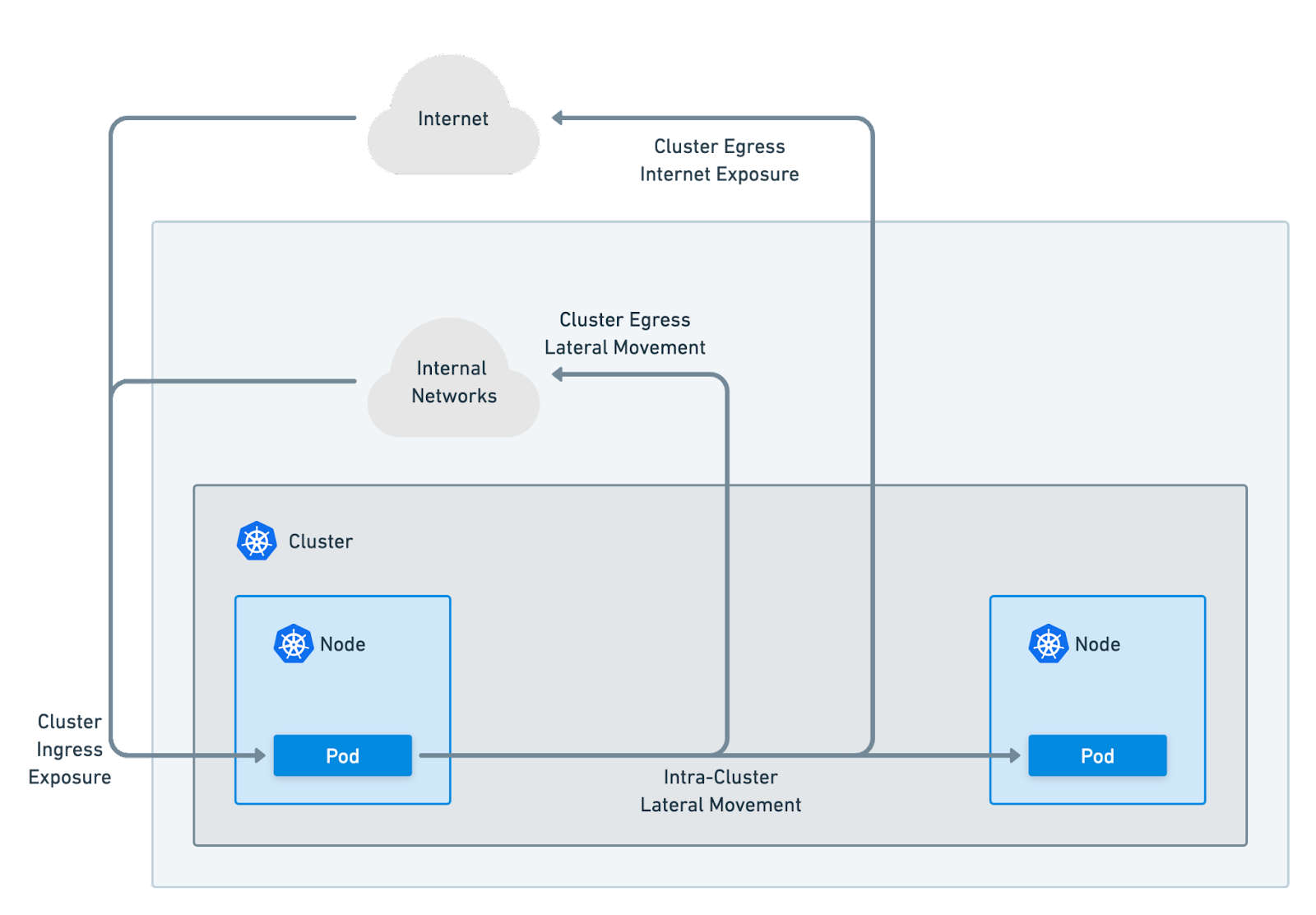
By moving from IP to identity, Cilium empowers you to free your security and operations teams from the need to manually review and audit every policy change. Cilium is natively integrated into the Kubernetes ecosystem aware of higher level identities, making it easier to weave compliance and security governance into the DevOps process. For example, operators can write network policies based on namespaces or labels rather hardcoding IPs. This integration helps maintain and enforce security and compliance standards throughout your DevOps processes.
Guru Ramamoorthy talks about how S&P Global’s network engineers leveraged eBPF-based networking with Cilium to connect and secure their clouds
Bloomberg leverages Cilium to construct data sandboxes that restrict users from exfiltrating data from the sandbox
Adelina Simon, a technology evangelist at Form3 talks about how they built a multi-cloud payments platform using Cilium

Cilium helped the Post Finance team build a scalable Kubernetes platform which meets the demanding requirements to run mission-critical banking software in production.
Watch The Case Study
Capital One leveraged Cilium to build a multi-tenant platform meeting all its requirements for security, maintainability, network visibility, and scale.
Watch The Talk
Robinhood's war stories from running Cilium in a high-churn near-production environment, learn how they overcame challenges by better understanding and tuning Cilium.
Watch The TalkElevate compliance and lower risk with Cilium transparent encryption. With just one switch, no application changes, service meshes or additional proxies
Learn moreMaintain identity based policies effectively at scale with Cilium’s advanced network polices
Learn morePresent a group of cloud native workloads from a stable IP address to integrate with traditional firewalls
Learn more